
Whaling attacks are a type of phishing attack that targets wealthy, prominent, and high-profile individuals such as CEOs, CFOs, and senior or high-level executives.
Definition of Whaling:
Whaling attack, also known as Whale phishing attack is a type of phishing attack that targets wealthy, prominent, and high-profile individuals such as CEOs, CFOs, and senior or high-level executives. Whaling attack targets high-profile targets because they’re likely to possess access to more confidential data, intellectual property, and other sensitive information. Whaling attacks are communications that appear to have come from senior members of a company that target other senior members or important individuals at an organization, with the aim of stealing money or sensitive information or gaining access to their computer systems for criminal purposes. Cybercriminals use the intelligence they find on the internet (often searching social media) to gain information on the people they are portraying and the people they are targeting. Whaling is similar to Phishing in that it uses methods such as email and website spoofing to trick a target into performing specific actions, such as revealing sensitive data or transferring money.
Whaling vs Phishing vs Spear Phishing
Phishing:
Includes any type of attack that tries to fool a victim into taking some action, including sharing sensitive information, like usernames, passwords, and financial records, installing malware, or completing fraudulent financial payment. Emails are typically sent to a large list of individuals, attempting to get one to bite.
Spear Phishing:
A more focused form of phishing. The cybercriminal has either studied up on the group or has gleaned data from social media sites to con users. A spear phishing email generally goes to one person or a small group of people, designed to get the single recipient to respond. Some form of personalization is included – perhaps the person’s name, or the name of a client.
Whaling:
A form of spear phishing that targets high-ranking victims within a company with highly personalized information.
Examples of Whaling in the Real World:
One notable whaling attack occurred in 2016 when a high-ranking employee at Snapchat received an email from an attacker pretending to be the CEO. The employee was tricked into giving the attacker employee payroll information to the scammer.
Another prominent attack also happened in 2016, where toy giant Mattel lost over $3 million after a senior finance executive fell victim. The email purported to come from the new CEO and requested a wire transfer.
Another tactic to whaling is when the attacker follows up an email received with a phone call confirming the email request. This is a social engineering tactic which could be described as cyber enabled fraud. The phone call serves the dual purpose of corroborating the email request and making the victim complacent about a possible cyber-attack as they have also had a 'real world' interaction.
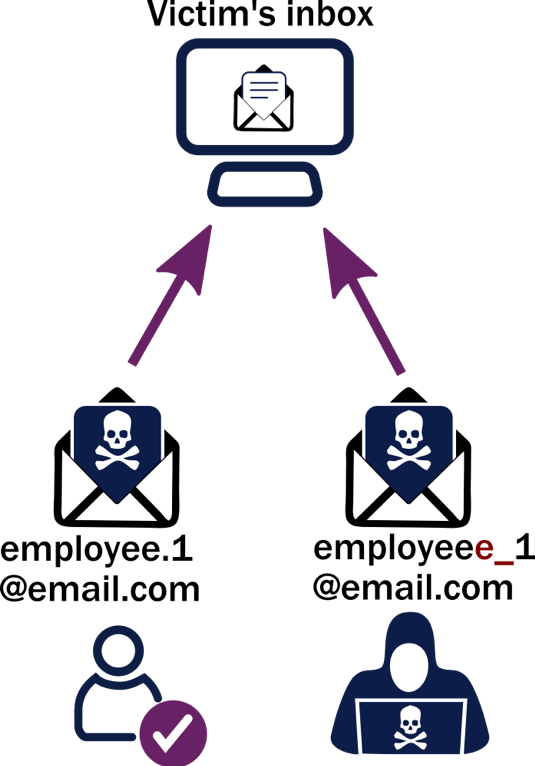
An attacker may also send from an email address that looks very close to the correct email address, a spoofed email address, to convince other employees they are receiving a legitimate request.
Prevent Whaling Attacks
- Flag emails that are sent from outside of the organization.
- Never click links or attachments in emails that come from anonymous sources.
- It is best to not respond to any emails that ask for personal or financial information.
- Establish a multi-step verification process for all requests for sensitive data or wire transfers.
- It is always best to verify the legitimacy of the source before responding to an email.
- High-level executives should take extra caution when posting and sharing personal information on social media sites such as Facebook, Twitter, and LinkedIn.
- Security researchers recommend educating employees on how to identify phishing emails.
- It is highly recommended to implement a good anti-phishing software